MUA (메일 사용자 기능 : 사용자의 메일을 저장 해 두는 기능 -> POST BOX에 저장 )
MTA ( 메일 전송 기능 : 목적지 서버로 전송 )
MDA ( 메일 전달 기능 : 특정 사용자에게 전달)
여기서 Send mail 은 이 3가지를 모두 가지고 있는 것이 특징입니다.
가. sendmail환경 설정
1. m4 를 이용한 sendmail.cf 수정 과정
- edit sendmail.mc ( Reference 2.sendmail.mc 수정 )
- m4 sendmail.mc > /etc/sendmail.cf
- /etc/rc.d/init.d/sendmail restart
2. sendmail.mc 수정
[ Korean White Domain 설정시]
FEATURE(dnsbl, `blackholes.mail-abuse.org', `Rejected - see http://www.mail-abuse.org/rbl/')dnl
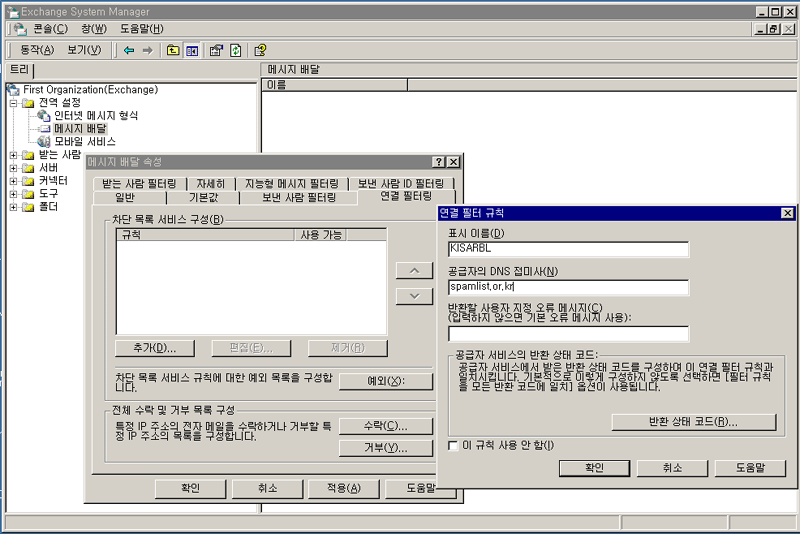
FEATURE(dnsbl, `spamlist.or.kr', `Rejected - see http://www.kisarbl.or.kr/')dnl
[Spam Filtering 해외 블랙 도메인 설정시]
FEATURE(`dnsbl', `relays.ordb.org', `"Rejected due to Open Relay see http://www.ordb.org/lookup/?host=" $& clientaddr} " for more information"')dnl
FEATURE(`dnsbl', `sbl.spamhaus.org', `"Rejected due to Spamhaus listing see http://www.abuse.net/sbl.phtml?IP=" $&{clientaddr} " for more information"')dnl
[To stop accepting E-mail from unresolvable domains ]
FEATURE(`accept_unresolvable_domains')dnl
[ Perpormance]
define(`confTO_CONNECT', `1m')dnl
define(`confTO_IDENT', `0')dnl
define(`confTO_COMMAND', `2m')dnl\
[ sudden mail flood ]
define(`confMAX_DAEMON_CHILDREN', 20)dnl
define(`confQUEUE_LA', `18')dnl
define(`confREFUSE_LA', `24')dnl
MAILER(smtp)dnl
MAILER(procmail)dnl
나. Sendmail 구동 환경 파일 수정
1. access.db 와 access 수정
- access.db 는 실제 메일을 전송하는 과정에서 전송을 할지 말지
전달할 경우에 대한 정의를 하는 것입니다. 아래 예제를 참고 하면 됩니다.
- access 파일을 수정후 make access.db 라는 명령으로 access.db를 업데이트 한다.
- sendmail 데몬을 리로딩한다.
참고 : relay-domains 설정:
relay-domains 파일은 가장 단순하게 relay를 제어하고 싶을 경우 사용하는 파일이다.
access.db를 사용하여 relay 컨트롤을 수행할 경우라면 relay-domains는 설정할 필요가 없다.
2. Configure access (/etc/mail/access)
#> cat /etc/mail/access
# Check the /usr/share/doc/sendmail/README.cf file for a description
# of the format of this file. (search for access_db in that file)
# The /usr/share/doc/sendmail/README.cf is part of the sendmail-doc
# package.
#
# by default we allow relaying from localhost...
localhost.localdomain RELAY # 내부에서 요청 된것은 모두 전달 한다.
localhost RELAY # sendmail의 내부 메커니즘은 로컬 루핑을 돌리면서 전송되도록 되어있서
127.0.0.1 RELAY # 이 3라인은 지우면 외부로 전달 혹은 전송이 되지 않을 수 있습니다.
#외부 서버에 대한 Relay 설정
192.168.0. RELAY # 로컬 사설망에서 요청된 메일은 모두 전달 한다.
www.goople.co.kr RELAY # 웹서버에서 메일 전송을 요청시 전달 한다.
#외부 서버에서 수신받을 도메인 설정
goople.co.kr OK # XXX@goople.co.kr 와 같은 goople.co.kr 도메인의 메일을 받아 들인다.
# 메 일중 반송할 규칙을 설정한다.
202.181.196. REJECT
friskycheese.com REJECT
From:elvisisthebomb.com REJECT
From:friskycheese.com REJECT
[참고]
1. http://www.revsys.com/writings/quicktips/sendmail-mc.html
2. http://myinfo.inempire.com/board/upload/technic/Linux/sendmail%208.12.8install.pdf
3. http://myhome.naver.com/tae7313/unix/unix-25.html
5. http://user.chol.com/~laday/solaris/sendmail.html
- Qmail 일 경우
var/qmail/rc.smtp(메일 서버 run 파일)
= 대체적으로 /var/qmail/supervise/qmail-smtpd 안의 run.sh
#!/bin/sh
QMAILDUID=`id -u qmaild`
NOFILESGID=`id -g qmaild`
exec /usr/local/bin/softlimit -m 5000000 \
/usr/local/bin/tcpserver -v -R -l 0 -x /etc/tcp.smtp.cdb \
-u "$QMAILDUID" -g "$NOFILESGID" 0 smtp /usr/local/bin/rblsmtpd -b -r spamlist.or.kr /var/qmail/bin/qmail-smtpd 2>&1
- Sendmail 일 경우
첫번째 방법: sendmail(8.9.x) - sendmail.cf 수정
# DNS based IP address spam list spamlist.or.kr
R$* $: $&{client_addr}
R::ffff:$-.$-.$-.$- $: $(host $4.$3.$2.$1.spamlist.or.kr. $: OK $)
R$-.$-.$-.$- $: $(host $4.$3.$2.$1.spamlist.or.kr. $: OK $)
ROK $: OK
R$+ $#error $@ 5.7.1 $: "550 Mail from " $&{client_addr} " refused by kisarbl site kisarbl.or.kr”
두번째 방법 : sendmail(8.10.x) - sendmail.mc 추가
FEATURE(dnsbl, `blackholes.mail-abuse.org', `Rejected - see http://www.mail-abuse.org/rbl/')dnl
FEATURE(dnsbl, `spamlist.or.kr', `Rejected - see http://www.kisarbl.or.kr/')dnl
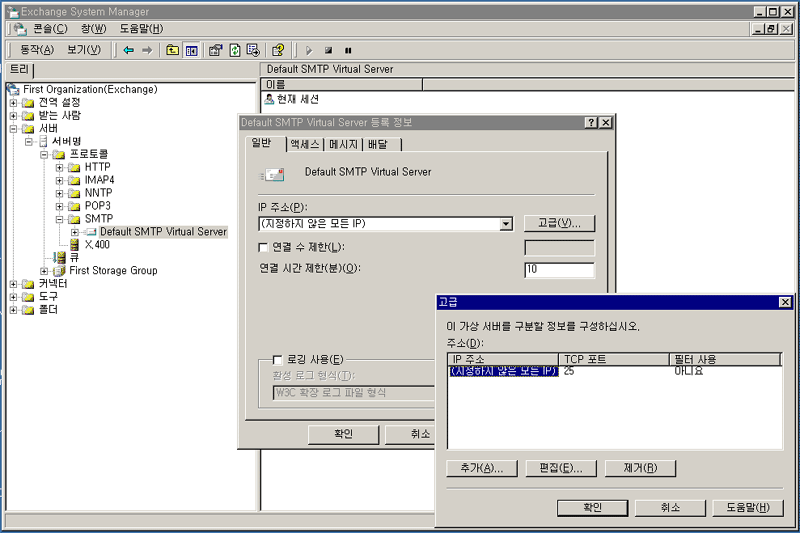
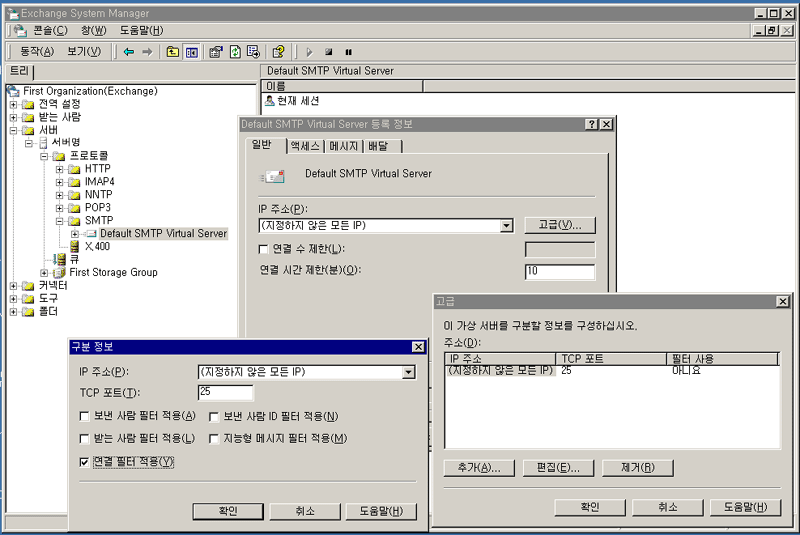
- EXCHANGE 의 경우
|
 How to use the SBL |
| The Spamhaus Block List ("SBL") can be used by almost all modern mail servers, by setting your mail server's anti-spam DNSBL feature (sometimes called "Blacklist DNS Servers" or "RBL servers") to query sbl.spamhaus.org. Use of the SBL is free for individuals operating small mail servers as long as your email traffic is low. Commercial users, corporate networks and ISPs need to purchase a yearly subscription to use the service: see DataFeed. For information on how to configure your mail server to use sbl.spamhaus.org please refer to your mail server documentation/manuals or ask your mail server developer. With so many different mail servers in use we can not offer technical help with setting up the SBL. DNSBL Queries We recommend you use sbl.spamhaus.org together with xbl.spamhaus.org, as the SBL and XBL block different spam sources. To save you having to query two separate DNSBL zones there is a special combined "SBL+XBL" zone, sbl-xbl.spamhaus.org, which contains the complete SBL and XBL data (we recommend you use this combined zone), to use it, simply set your mail server's DNSBL check to query sbl-xbl.spamhaus.org only. Not just for connection queries... In addition to checking the IPs of the connecting servers against the SBL, you can significantly boost your spam catch rate by also scanning the email body of any mails that get past SBL/XBL looking for host names of URLs (web sites) advertised in spams, and checking the IPs of those hosts, and their names servers, against the SBL. This is because the SBL lists the IPs of spammers' websites in addition to their mail servers. This feature ("URIBL_SBL") is available in SpamAssassin 3.0, and code to do this is also available as a sendmail milter from here. Data Feed: Zone Transfers (rsync) for Corporate networks & ISPs For corporate users and Internet Service Providers Spamhaus provides a dedicated Data Feed service which transfers the Spamhaus DNSBL zones to a local DNS server on your network and keeps the zones synchronised every 30 minutes. To submit an application for this service see: Data Feed Application Form. Testing your SBL Setup Once you have set up your mail server to use sbl.spamhaus.org, you can test to see if the SBL blocking is working by sending an email (any email) to: nelson-sbl-test@crynwr.com (you must send the email from the mail server which you wish to test). The Crynwr system robot will answer you to tell you if your server is correctly blocking SBL-listed IPs or not. |



댓글