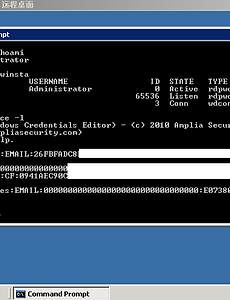
 Windows Credentials Editor v1.0
Supports Windows XP, 2003, Vista, 7 and 2008 (Vista was not actually tested yet, but it should work).Windows Credentials Editor (WCE) allows to list logon sessions and add, change, list and delete associated credentials (ex.: LM/NT hashes). This can be used, for example, to perform pass-the-hash on Windows and also obtain NT/LM hashes from memory (from interactive logons, services, remote deskto..
2010. 12. 1.
Windows Credentials Editor v1.0
Supports Windows XP, 2003, Vista, 7 and 2008 (Vista was not actually tested yet, but it should work).Windows Credentials Editor (WCE) allows to list logon sessions and add, change, list and delete associated credentials (ex.: LM/NT hashes). This can be used, for example, to perform pass-the-hash on Windows and also obtain NT/LM hashes from memory (from interactive logons, services, remote deskto..
2010. 12. 1.